AidenWyatt04
Registered
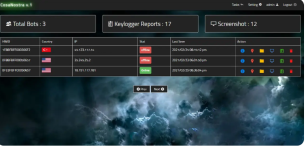
Features:
- Keylogger: Captures keystrokes to steal sensitive information like passwords.
- Clipper: Replaces cryptocurrency wallet addresses in the clipboard to redirect funds.
- Screenshot Stealer: Captures screenshots of the victim's device.
- File Stealer: Extracts files such as photos, documents, and text files from the victim's device.
- Download and Execute (Loader): Downloads and runs malicious files or payloads on the infected system.
- Device Information Gathering: Collects details like PC name, operating system, firewall status, RAM, antivirus software, and processor information.
- Location and Address Retrieval: Obtains the geographical location and IP address of the victim.
- Browser Data Clearing: Clears cookies and sessions from 20 browsers, including Google Chrome, Mozilla Firefox, Opera, and Yandex.
- Anti-Sandbox Protection: Evades detection by tools like Wireshark, Process Hacker, TCPView, VirtualBox, and Sandboxie.
- Web Panel Features:
- Dynamic and Responsive Pages: Accessible from mobile devices for ease of use.
- Home Page: Displays all bots, counters for keylogger reports and screenshots, and details like HWID, country IP, online/offline status, and last seen.
- Settings Page: Allows customization of operational timing and activation of file-stealing features.
- Tasks Page: Enables adding or deleting tasks, such as downloading and executing files.
- User Page: Facilitates changing user information for the botnet operator.





