ZoeWillow22
Registered
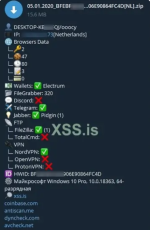
Targeted Applications & Data Sources
- Steals saved passwords from web browsers like Chrome, Firefox, Edge.
- Captures clipboard contents (copied text, often used to grab crypto wallet addresses).
- Extracts data from Discord, Telegram, Outlook, and other messaging apps.
- Grabs credentials from FTP clients such as FileZilla and Total Commander.
- Steals chat credentials from apps like Pidgin, Psi, and Psi+.
- Targets and steals data from cryptocurrency wallets:
- Bitcoin Core
- Electrum
- Exodus
- Ethereum
- Monero
- Litecoin
- Dash
- Zcash
- Atomic
- Jaxx
- And others
- Extracts login data and configuration from VPNs:
- NordVPN
- ProtonVPN
- OpenVPN
- Captures system information (hardware and OS details).
- Takes screenshots silently during infection.
- Scans for and steals specific file types from user directories (like .txt, .docx, .wallet, etc.).
- Sends stolen data via Telegram bot or other channels.
- Built-in feature for auto-deletion after completing the steal operation to reduce detection.
- Avoids uploading duplicate logs (helps reduce noise and detection).
- Often packed or obfuscated to avoid antivirus detection.




